Business Partner Federation
Introduction
Business Partner Federation establishes a trust relationship between the Service Provider (SP) and Identity Provider (IDP) using SAML tokens. By establishing this trust relationship, you can enable users to access your resources as well as partner resources with a single set of credentials.
This page introduces two use cases for business partner federation, discusses the responsibilities between partners, and shows how to set up business partner federation in Centrify both via the admin portal, and programmatically using the Centrify REST API.
Use Cases
There are two use cases for Business Partner Federation.
Use Case 1 - Tenant to Business Partner
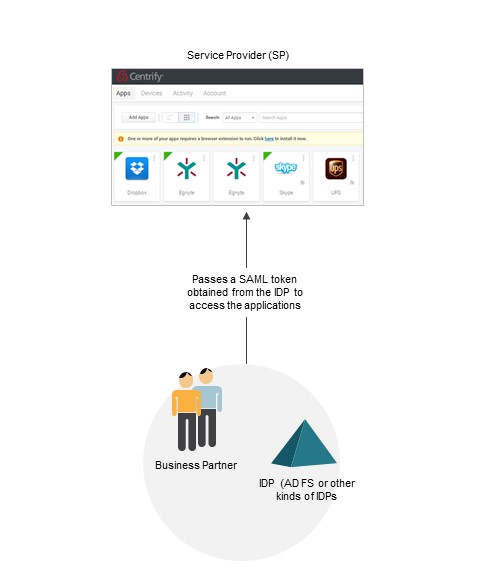
In this use case, you share your Centrify tenant (Centrify Identity Services/Centrify Privilege Service) with your business partners. Your Centrify tenant (which hosts the services/applications) serves as the SP and your partner serves as the IDP. Your business partners access the tenant and its associated resources/applications by passing a SAML token obtained from their IDP service. This use case applies to any IDP (AD FS or other kinds of IDPs).
Use Case 2 - Tenant to Tenant
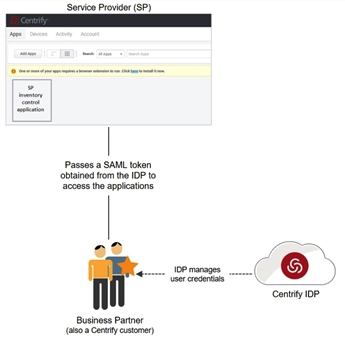
This use case is sometimes referred to as “tenant to tenant” because both the SP and IDP are Centrify tenants. Your business partners access the resources/applications by passing a SAML token obtained from their Centrify IDP tenant.
Responsibilities
This section lists the elements that partners and service providers must exchange or configure in order to set up business partner federation.
Partners are responsible for the following:
- Providing you with their IDP metadata.
- Providing you with the group attribute value(s) they will pass in their SAML tokens. See Mapping External Role-Based values to Group Attribute Values.
- Configuring their IDP to pass SAML tokens to you:
- If your partner is using an external IDP, see our support Knowledge Base article for ADFS configuration information.
- If your partner is using another Centrify tenant, they can easily do this by deploying the Centrify B2B SAML application. See Custom SAML applications.
Service Providers (SPs) are responsible for the following:
- Providing the SP metadata to your partner. See Providing the Service Provider metadata.
- Adding the partner in Admin Portal. See Adding a Partner. You will need the IDP metadata and the group attribute value from your partner before you can complete this task.
- Assigning your groups to roles in Admin Portal. See Assigning Host Groups to Roles.
- Mapping of the global group attribute (for all your partners) to your groups. See Mapping of Global Group Attributes.
- Specifying multi-factor authentication (MFA) for partner logins. See Specifying Partner MFA Requirements.
The following sections provide more information about how to configure and retrieve these elements.
Mapping External Role-Based Values to Group Attribute Values
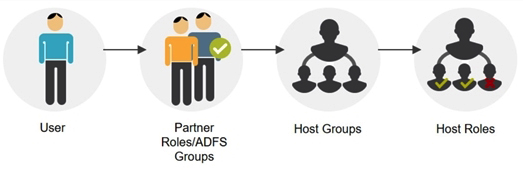
As part of managing their users, partners typically assign them role-based values (also known as group attribute values), such as Sales Managers, Service Managers, etc. However, Centrify does not have visibility into their user directories nor their naming conventions. For example, one partner may name the value "Sales Managers" while another partner may name it "SalesTeamManagers".
To organize these group attribute values, Centrify has created a “group” construct in the federated directory service. As a systems administrator in the host tenant, you can create host groups (e.g. "Mgrs-Sales" group) in which to map the group attribute values (for example the "Sales Managers" and "SalesTeamManagers" values). This host group can then be added to roles in your tenant. The diagram below demonstrates this flow.
See Mapping of Global Group Attributes for information on how to set this up.
Adding a Partner
There are two ways to add a partner. You can add the partner in Admin Portal to enable sharing on your end. You will need the group attribute values and IDP metadata from your partner to finish the configuration. You can also add the partner programmatically, using Federation APIs.
Before you begin, ensure you have the following from your partner(s).
- Partner roles/ADFS groups
- IDP metadata
Adding a Partner in the Admin Portal
- Log in to the Admin Portal.
- Click Settings > Users > Partner Management > Add. The Partner Management popup appears.
- Enter a unique partner name.
- Leave the Federation Type as SAML2.0. SAML 2.0 is selected because Centrify currently only supports this federation type.
- Enter a unique domain name under Federation Domains and click Add.This domain name will be used as the login suffix for all partner users. It allows Centrify to recognize users as coming from a specific IDP and redirects them accordingly. For example, you may want to use the business partner company name (e.g., example companyABC.com) as the domain name.
- Click Group Mappings > Add to create a mapping of the group attribute values (i.e., partner roles for other Centrify tenants, or groups for partners using ADFS) to your groups.
- Enter the partner role or ADFS group (ADFS federation) into the Group Attribute Value column and then select an existing group in the Group Name column or enter a new name.
This step maps the partner roles/ADFS groups (provided by your partner) to your groups. Each group needs to be a member of at least one role in your tenant. See Assigning Host Groups to Roles for more information. - Click Inbound Metadata to configure IDP settings using the IDP metadata from your partner. This screen provides the following options to enter metadata:
- Option 1: Upload the IDP configuration from URL. To use this option, paste the Identity Provider SAML Metadata URL provided by your partner.
- Option 2: Upload IDP configuration from a file. If your partner provided the Identity Provider SAML Metadata in an XML file, you can upload it here.
- Option 3: Manually enter the information. This is not a recommended option.
Adding a Partner Programmatically Using the ederation APIs
- Invoke the /federation/GetGroups endpoint to get a list of existing federation groups:
POST https://mytenant.my.centrify.com/Federation/GetGroupsThe Result field in the response contains the names of the federation groups:
{
"success":true,
"Result":[
"TestB2B",
"Office365Users"
],
"Message":null,
...
}- Invoke the /federation/GetGlobalFederationSettings endpoint to obtain the SP federation information:
POST https://mytenant.my.centrify.com/Federation/GetGlobalFederationSettings?FederationType=SAML%202.0The response contains the SP information:
{
"success":true,
"Result":{
"GlobalMappings":[
{
"Team":"TestB2B"
}
],
"SPAutnenticationResponseUrl":"https://mytenant.centrify.com/My",
"SPMetadataUrl":"https://mytenant.centrify.com/Federation/federationmetadata?FederationType=SAML%202.0",
"SPSigningCertificateCAExpires":"1/1/2039 12:00:00 AM",
"SPSigningCertificateCASubject":"CN=Centrify Customer mytenant",
"SPSigningCertificateCAThumbprint":"5135A...",
"SPSigningCertificateCAUrl":"https://mytenant.centrify.com/Federation/SPSigningCertificateAuthority",
"SPSigningCertificateExpires":"1/1/2039 12:00:00 AM",
"SPSigningCertificateSubject":"CN=Centrify Customer mytenant Application Signing Certificate",
"SPSigningCertificateThumbprint":"9AF288490...",
"SPSigningCertificateUrl":"https://mytenant.centrify.com/Federation/SPSigningCertificate",
"IDPEndpointUrl":"https://mytenant.centrify.com",
"RequestedAttributes":[
"Description",
"DisplayName",
"EmailAddress",
"Group",
"HomeNumber",
"LoginName",
"MobileNumber",
"Name",
"OfficeNumber",
"Photo",
"UserPrincipalName"
],
"SPLogoutUrl":"https://mytenant.centrify.com/Security/Logout",
"SPLogoutReturnUrl":"https://mytenant.centrify.com/My"
},
"Message":null,
"MessageID":null,
...
}- Invoke the /federation/CreateFederation endpoint to create a new federation. In the following example, the metadata information is passed by an embedded xml file:
POST https://mytenant.centrify.com/Federation/CreateFederation
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="FederationName"
JamesTest
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="FederationType"
SAML 2.0
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="Domains"
jamestest.com
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="Name"
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="Mappings"
[{"AttributeValue":"attr1","GroupName":"TestB2B","undefined":""}]
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="IDPMetadataUrl"
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="IDPSignInUrl"
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="IDPLogoutUrl"
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="IDPSigningCert_name"
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="IDPSigningCertPassword"
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="FederationUuid"
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="IDPSigningCertificateThumbprint"
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="IsMetaData"
true
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="SPMetadataUrl"
https://mytenant.centrify.com/Federation/federationmetadata?FederationType=SAML%202.0
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="SPAutnenticationResponseUrl"
https://mytenant.centrify.com/My
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="SPSigningCertificate_name"
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="SPSigningCertificateCA_name"
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="IDPMetadataFileContents"; filename="Centrify B2B - IdP Metadata.xml"
Content-Type: text/xml
<EntityDescriptor xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" entityID="https://mytenant.centrify.com/23c851de-2ece-4577-97c7-2dbef900b7de" xmlns="urn:oasis:names:tc:SAML:2.0:metadata"><IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"><KeyDescriptor><KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#"><X509Data><X509Certificate>MII0../run?appkey=23c851...&customerId=mytenant" /><Attribute Name="Email Address" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic" xmlns="urn:oasis:names:tc:SAML:2.0:assertion" /></IDPSSODescriptor></EntityDescriptor>
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="IDPSigningCert"; filename=""
Content-Type: application/octet-stream
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="SPSigningCertificate"; filename=""
Content-Type: application/octet-stream
------WebKitFormBoundary1KzYohanYBeThORE
Content-Disposition: form-data; name="SPSigningCertificateCA"; filename=""
Content-Type: application/octet-stream
------WebKitFormBoundary1KzYohanYBeThORE--The Result field in the response contains the information for the new federation:
{
"success":true,
"Result":{
"NormalizedFederationName":"acmeco",
"FederationName":"acmeco",
"Config":{
"SPSigningCertificateThumbprint":"9AF288...",
"IDPMetadataUrl":"",
"IDPSigningCertificateThumbprint":"D8DFB9...",
"IDPSigningCertificateSubject":"CN=Centrify Customer mytenant Application Signing Certificate",
"IDPSignInUrl":"https://my.centrify.com/run?appkey=23c851...&customerId=mytenant",
"SPSigningCertificateSubject":"CN=Centrify Customer mytenant Application Signing Certificate",
"SPSigningCertificateExpires":"1/1/2039 12:00:00 AM",
"IDPSigningCertificateCollection":[
{
"IDPSigningCertificateExpires":"1/1/2039 12:00:00 AM",
"IDPSigningCertificateSubject":"CN=Centrify Customer mytenant Application Signing Certificate",
"IDPSigningCertificateThumbprint":"D8DFB92C..."
}
],
"IDPSigningCertificateExpires":"1/1/2039 12:00:00 AM",
"IDPLogoutUrl":"https://my.centrify.com/applogout/appkey/23c85.../customerid/mytenant"
},
"Domains":[
"jamestest.com"
],
"DirectLoginSupported":true,
"Active":true,
"PartnerManageable":true,
"FederationType":"SAML 2.0",
"FederationUuid":"0af846...",
"Mappings":[
{
"AttributeValue":"attr1",
"GroupName":"RyanB2B"
}
]
},
"Message":null,
...
}Assigning Host Groups to Roles
For the host groups to access relevant applications and rights, you need to assign them to the relevant roles. Host groups are listed in the Group Name column on Settings > Users > Partner Management > Group Mappings.
Assigning the Groups to Roles in the Admin Portal
- Log into the Admin Portal.
- Click Roles and select an existing role or create a new one.
- Click Members > Add and search for the group.
- In the Source area, you must have the FDS user source selected to see the federated users/groups. Groups from federated services have the icon shown below/FDS label associated:

- Select the group and click Add.
- Click Save.
Programmatically Assigning the Groups to Roles
- Invoke the /Redrock/query endpoint with the following query to obtain the roles:
POST https://mytenant.centrify.com/RedRock/query
{
"Script":"Select ID, COALESCE(Name, ID) AS Name, RoleType, ReadOnly, Description, DirectoryServiceUuid from Role ORDER BY Name COLLATE NOCASE",
"Args":{
"PageNumber":1,
"PageSize":100,
"Limit":100000,
"SortBy":"",
"direction":"False",
"Caching":-1
}
}The Results field in the response contains the list of roles:
{
"success":true,
"Result":{
"IsAggregate":false,
"Count":29,
"Columns":[
{
"Name":"ID",
"IsHidden":false,
"DDName":"_ID",
"Title":"ID",
"DDTitle":"ID",
"Description":"Row Identifier (primary key)",
"Type":12,
"Format":null,
"Width":0,
"TableKey":"Primary",
"ForeignKey":null,
"TableName":"Role"
},
],
"FullCount":29,
"Results":[
{
"Entities":[
{
"Type":"Role",
"Key":"21cb...",
"IsForeignKey":false
}
],
"Row":{
"Name":"AdminUsers",
"ID":"21cb...",
"Description":"AdminUsers",
"RoleType":"PrincipalList",
"ReadOnly":false,
"DirectoryServiceUuid":"09B9A..."
}
},
...
],
"ReturnID":""
},
"Message":null,
"MessageID":null,
"Exception":null,
"ErrorID":null,
"ErrorCode":null,
"InnerExceptions":null
}- Invoke the /Core/GetDirectoryServices endpoint to get a list of directory services:
POST https://mytentant.centrify.com/core/GetDirectoryServicesThe response contains the list of services:
{
"success":true,
"Result":{
"IsAggregate":false,
"Count":3,
"Columns":[
...
],
"FullCount":3,
"Results":[
{
"Entities":[
{
"Type":"DirectoryServices",
"Key":"??",
"IsForeignKey":false
}
],
"Row":{
"Service":"CDS",
"DisplayName":"Centrify Centrify Directory",
"Tenant":"mytenant",
"Name":"CDS",
"Status":"Active",
"Config":"Centrify Directory",
"StatusDisplay":"Online",
"Everybody":true,
"Description":"Centrify Directory",
"DisplayNameShort":"Centrify Directory",
"directoryServiceUuid":"09B9A..."
}
},
{
"Entities":[
{
"Type":"DirectoryServices",
"Key":"??",
"IsForeignKey":false
}
],
"Row":{
"Service":"AdProxy",
"DisplayName":"Active Directory: CentrifyTest.lab",
"Tenant":"mytenant",
"Name":"AdProxy_MyTest.lab",
"Status":"Inactive",
"Config":"MyTest.lab",
"StatusDisplay":"Offline",
"Everybody":true,
"Description":"Active Directory",
"DisplayNameShort":"AD: MyTest.lab",
"directoryServiceUuid":"3e98c...",
"Forest":"CentrifyTest.lab"
}
},
{
"Entities":[
{
"Type":"DirectoryServices",
"Key":"??",
"IsForeignKey":false
}
],
"Row":{
"Service":"FDS",
"DisplayName":"Federated Directory Service",
"Tenant":"mytenant",
"Name":"FDS",
"Status":"Active",
"Config":"Federated Directory Service",
"StatusDisplay":"Online",
"Everybody":true,
"Description":"Federated Directory",
"DisplayNameShort":"FDS",
"directoryServiceUuid":"C30B30..."
}
}
],
"ReturnID":""
},
"Message":null,
...
}- Invoke the /UserMgmt/DirectoryServiceQuery endpoint, passing the UUIDs of the directory services of interest to get the entities assigned to those services:
POST https://mytenant.my.centrify.com//UserMgmt/DirectoryServiceQuery
{
"user":"{\"_and\":[{\"_or\":[{\"DisplayName\":{\"_like\":\"a\"}},{\"givenName\":{\"_like\":\"a\"}},{\"sn\":{\"_like\":\"a\"}},{\"SystemName\":{\"_like\":\"a\"}}]},{\"ObjectType\":\"user\"}]}",
"directoryServices":[
"09B9A9...",
"C30B30..."
],
"group":"{\"_or\":[{\"DisplayName\":{\"_like\":\"a\"}},{\"SystemName\":{\"_like\":\"a\"}}]}",
"roles":"{\"_or\":[{\"_ID\":{\"_like\":\"a\"}},{\"Name\":{\"_like\":\"a\"}}]}",
"Args":{
"PageNumber":1,
"PageSize":100000,
"Limit":100000,
"SortBy":"",
"direction":"False",
"Caching":-1
}
}The Result field in the response contains the directory service entities:
{
"success":true,
"Result":{
"roles":{
"IsAggregate":false,
"Count":2,
"Columns":[
...
],
"FullCount":2,
"Results":[
...
],
"ReturnID":""
},
"Group":{
"IsAggregate":false,
"Count":0,
"Columns":[
...
],
"FullCount":0,
"Results":[
],
"ReturnID":""
},
"User":{
"IsAggregate":false,
"Count":3,
"Columns":[
...
],
"FullCount":3,
"Results":[
{
"Entities":[
{
"Type":"f0f35...",
"Key":"User",
"IsForeignKey":false
}
],
"Row":{
"Description":null,
"DisplayName":"Cloud Admin",
"ObjectType":"User",
"DistinguishedName":"[email protected]",
"DirectoryServiceUuid":"09B9A...",
"SystemName":"[email protected]",
"ServiceInstance":"CDS",
"Locked":false,
"InternalName":"f0f350...",
"StatusEnum":"Active",
"ServiceInstanceLocalized":"Centrify Directory",
"ServiceType":"CDS",
"Forest":"",
"EMail":"[email protected]",
"Status":"Active",
"Enabled":true
}
},
...
],
"ReturnID":""
}
},
"Message":null,
...
}- Invoke the /saasManage/StoreRole endpoint to add a new role:
POST https://mytenant.centrify.com/saasManage/StoreRole
{
"Name":"NewRole"
}The _rowKey field in the response contains the UUID of the newly created role:
{
"success":true,
"Result":{
"_RowKey":"9390..."
},
"Message":null,
"MessageID":null,
"Exception":null,
"ErrorID":null,
"ErrorCode":null,
"InnerExceptions":null
}- Invoke the /saasManage/GetRole endpoint to obtain the details for the newly created row. Pass the UUID from the previous response via the name parameter:
POST https://mytenant.centrify.com/saasManage/GetRole
{
"name":"9390...",
"suppressPrincipalsList":true,
"Args":{
"PageNumber":1,
"Limit":1,
"PageSize":1,
"Caching":-1
}
}- Invoke the /saasManage/UpdateRole endpoint to add a role to the desired user. Pass the role ID via the Name field:
POST https://mytenant.com/Roles/UpdateRole
{
"Users":{
"Add":[
"f0f350..."
]
},
"Name":"9390..."
}The success field in the response indicates if the request was successful:
{
"success":true,
"Result":null,
"Message":null,
"MessageID":null,
"Exception":null,
"ErrorID":null,
"ErrorCode":null,
"InnerExceptions":null
}Mapping of Global Group Attributes
You can create a mapping of global group attribute values for all your partners (i.e., partner roles for Centrify Identity Services tenants, or groups for partners using ADFS) to your specified groups. If the system encounters conflicts, the individual group attribute mapping takes priority.
Before you begin, ensure you have the partner roles/ADFS groups information from your partner(s).
Mapping Global Group Attributes to Your Specified Groups in the Admin Portal
- Log into the Admin Portal.
- Click Settings > Users > Partner Management > Global Mappings > Add.
- Enter the global partner role or ADFS group (ADFS federation) into the Group Attribute Value field.
- Select an existing group in the Group Name text box or enter a new name.
This procedure maps global partner roles/ADFS groups (provided by your partners) to your groups. Each group needs to be a member of at least one role in your tenant. See Assigning Host Groups to Roles. - Click OK.
Programmatically Mapping Global Group Attributes to Your Specified Groups
- Invoke the /federation/AddGlobalGroupAssertionMapping endpoint and pass in the group attribute value for the key and the group name for the value:
POST https://mytenant.centrify.com/Federation/AddGlobalGroupAssertionMapping
{
"attr1":"B2BGroup"
}Note: You can get a list of group names programmatically using the /federation/GetGlobalGroupAssertionMappings endpoint.
The success field in the response indicates if the request was successful:
{
"success":true,
"Result":null,
"Message":null,
...
}Providing the Service Provider Metadata
Provide your partner with your service provider metadata.
Getting the Service Provider Metadata in the Admin Portal:
- Click Settings in the Admin Portal.
- Click Users > Partner Management and ensure the Partners tab is selected.
- If you have not started creating the partner profile, click Add to access the necessary information. If you have an existing partner, you can look at that partner's information for the service provider metadata. The same metadata information is provided to all of your partners.
- Click Outbound Metadata and use one of the three options to get the metadata information.
Programmatically Getting the Service Provider Metadata:
- Invoke the /federation/GetGlobalFederationSettings endpoint setting the Federation query parameter to
SAML%202.0:
POST https://mytenent.centrify.com/Federation/GetGlobalFederationSettings?FederationType=SAML%202.0The Result field response contains the SP metadata:
{
"success":true,
"Result":{
"GlobalMappings":[
{
"Team":"AcmeB2B"
} ],
"SPAutnenticationResponseUrl":"https://mytenant.centrify.com/My",
"SPMetadataUrl":"https://mytenant.centrify.com/Federation/federationmetadata?FederationType=SAML%202.0",
"SPSigningCertificateCAExpires":"1/1/2039 12:00:00 AM",
"SPSigningCertificateCASubject":"CN=Centrify Customer AAH0191",
"SPSigningCertificateCAThumbprint":"5135AA",
"SPSigningCertificateCAUrl":"https://mytenant.centrify.com/Federation/SPSigningCertificateAuthority",
"SPSigningCertificateExpires":"1/1/2039 12:00:00 AM",
"SPSigningCertificateSubject":"CN=Centrify Customer AAH0191 Application Signing Certificate",
"SPSigningCertificateThumbprint":"9AF288",
"SPSigningCertificateUrl":"https://mytenant.centrify.com/Federation/SPSigningCertificate",
"IDPEndpointUrl":"https://mytenant.centrify.com",
"RequestedAttributes":[
"Description",
"DisplayName",
"EmailAddress",
"Group",
"HomeNumber",
"LoginName",
"MobileNumber",
"Name",
"OfficeNumber",
"Photo",
"UserPrincipalName"
],
"SPLogoutUrl":"https://mytenant.centrify.com/Security/Logout",
"SPLogoutReturnUrl":"https://mytenant.centrify.com/My"
},
"Message":null,
...
}Specifying Partner MFA Requirements
This configuration is optional for Service Providers (SP).
As an SP, you can require that your business partners meet additional authentication requirements before they can access the resources/applications hosted on your Centrify tenant. For example, you can require that your partner authenticate by answering a security question. This additional requirement ensures that the partner user is using multi-factor authentication (MFA) to access your Centrify tenant.
Specifying Additional Authentication Requirements in the Admin Portal
- Log in to the Admin Portal.
- Click Core Services > Policies.
- Select the relevant policy set.
- Click Login Policies > Centrify Portal.
- Define the authentication requirements you want your partner users to meet. See How to Define Authentication Requirements.
We recommend that you do not define password as one of the additional authentication mechanisms. Centrify Identity Services assumes that your partners are logging in using a username/password. If you specify password as one of the authentication mechanism, it will be ignored. For example, if you choose an authentication profile with phone call and password as the authentication mechanisms, the partner user will only be authenticated using phone call.
- Enable the Apply additional authentication rules to federated users checkbox in the Other Settings section.
- Click Save.
Programmatically Specifying Additional Authentication Requirements
- Invoke the /Policy/GetNicePlinks endpoint to obtain the existing policy information:
POST https://mytenant.centrify.com/policy/getniceplinks
{
"Args":{
"PageNumber":1,
"PageSize":100000,
"Limit":100000,
"SortBy":"",
"direction":"False",
"Caching":-1
}
}The response contains the policy information:
{
"success":true,
"Result":{
"Columns":[
...
],
"RevStamp":"636724483080000000",
"Count":3,
"Results":[
{
"Entities":[
{
"Type":"PolicyLink",
"Key":"/Policy/PolicySet_1",
"IsForeignKey":false
}
],
"Row":{
"Params":[
],
"ID":"/Policy/PolicySet_1",
"EnableCompliant":true,
"Description":"",
"LinkType":"Global",
"PolicySet":"/Policy/PolicySet_1"
}
},
{
"Entities":[
{
"Type":"PolicyLink",
"Key":"/Policy/MDM and WSTrust and Login",
"IsForeignKey":false
}
],
"Row":{
"Params":[
],
"ID":"/Policy/MDM and WSTrust and Login",
"EnableCompliant":true,
"Description":"This will provide settings for the various user login possibilities and MDM device profile, and allows WS-Trust",
"LinkType":"Global",
"PolicySet":"/Policy/MDM and WSTrust and Login"
}
},
{
"Entities":[
{
"Type":"PolicyLink",
"Key":"/Policy/Default Policy",
"IsForeignKey":false
}
],
"Row":{
"Params":[
],
"ID":"/Policy/Default Policy",
"EnableCompliant":true,
"I18NDescriptionTag":"_I18N_DefaultGlobalPolicyDescriptionTag",
"Description":"Enables password recovery and Samsung KNOX Workspace containers.\n\nRequests for password recovery will be validated via SMS or email verification.\nKNOX Workspace containers will be created automatically upon enrollment of a compatible device.",
"LinkType":"Inactive",
"PolicySet":"/Policy/Default Policy"
}
}
],
"FullCount":3,
"ReturnID":"",
"IsAggregate":false
},
"Message":null,
...
}- Using the information from the previous response, update the information and invoke the /policy/SavePolicyBlock3 endpoint passing in the updated policy information via the request body:
POST https://mytenant.centrify.com/policy/savepolicyblock3
{
"plinks":[
{
"Description":"",
"PolicySet":"/Policy/PolicySet_2",
"LinkType":"Global",
"Priority":1,
"Params":[
],
"Filters":[
],
"Allowedpolicies":[
]
},
{
"Params":[
],
"ID":"/Policy/PolicySet_1",
"EnableCompliant":true,
"Description":"",
"LinkType":"Global",
"PolicySet":"/Policy/PolicySet_1"
},
{
"Params":[
],
"ID":"/Policy/MDM and WSTrust and Login",
"EnableCompliant":true,
"Description":"This will provide settings for the various user login possibilities and MDM device profile, and allows WS-Trust",
"LinkType":"Global",
"PolicySet":"/Policy/MDM and WSTrust and Login"
},
{
"Params":[
],
"ID":"/Policy/Default Policy",
"EnableCompliant":true,
"I18NDescriptionTag":"_I18N_DefaultGlobalPolicyDescriptionTag",
"Description":"Enables password recovery and Samsung KNOX Workspace containers.\n\nRequests for password recovery will be validated via SMS or email verification.\nKNOX Workspace containers will be created automatically upon enrollment of a compatible device.",
"LinkType":"Inactive",
"PolicySet":"/Policy/Default Policy"
}
],
"policy":{
"Path":"/Policy/PolicySet_2",
"Version":1,
"Description":"",
"Settings":{
"AuthenticationEnabled":true,
"/Core/Authentication/AuthenticationRulesDefaultProfileId":"29e368...",
"/Core/Authentication/CookieAllowPersist":false,
"/Core/Authentication/AllowIwa":true,
"/Core/Authentication/IwaSetKnownEndpoint":false,
"/Core/Authentication/IwaSatisfiesAllMechs":false,
"/Core/Authentication/AllowZso":true,
"/Core/Authentication/ZsoSetKnownEndpoint":false,
"/Core/Authentication/ZsoSatisfiesAllMechs":false,
"/Core/Authentication/NoMfaMechLogin":false,
"/Core/Authentication/FederatedLoginAllowsMfa":true,
"/Core/MfaRestrictions/BlockMobileMechsOnMobileLogin":false,
"/Core/Authentication/ContinueFailedSessions":true,
"/Core/Authentication/SkipMechsInFalseAdvance":true
},
"Newpolicy":true
}
}The success field in the response indicates if the response was successful and the RevStamp field contains the revision number of the updated policy information:
{
"success":true,
"Result":{
"RevStamp":"636724699540000000"
},
"Message":null,
"MessageID":null,
"Exception":null,
"ErrorID":null,
"ErrorCode":null,
"InnerExceptions":null
}Updated 4 months ago
